"Just Click Allow": The Silent Security Threat of Calendar Integrations
When a vendor asks for "Read/Write" access to your calendar, they aren't just asking to book meetings. They are asking for the keys to your organization's most sensitive metadata.
In the rush to automate scheduling, it is easy to overlook the technical implications of that "Sign in with Google" or "Connect Outlook" button. For most end-users, it is a 5-second friction point. For an IT security architect, it should be a red flag requiring immediate audit.
The core issue lies in OAuth Scopes. Most scheduling tools request broad permissions because it is easier for their developers to ask for "everything" than to build granular, least-privilege integrations. This article explains what you are actually granting, and how to push back.
This is a technical deep-dive supplementing our broader Enterprise Procurement Guide.
The "Read/Write" Trap: What It Really Means
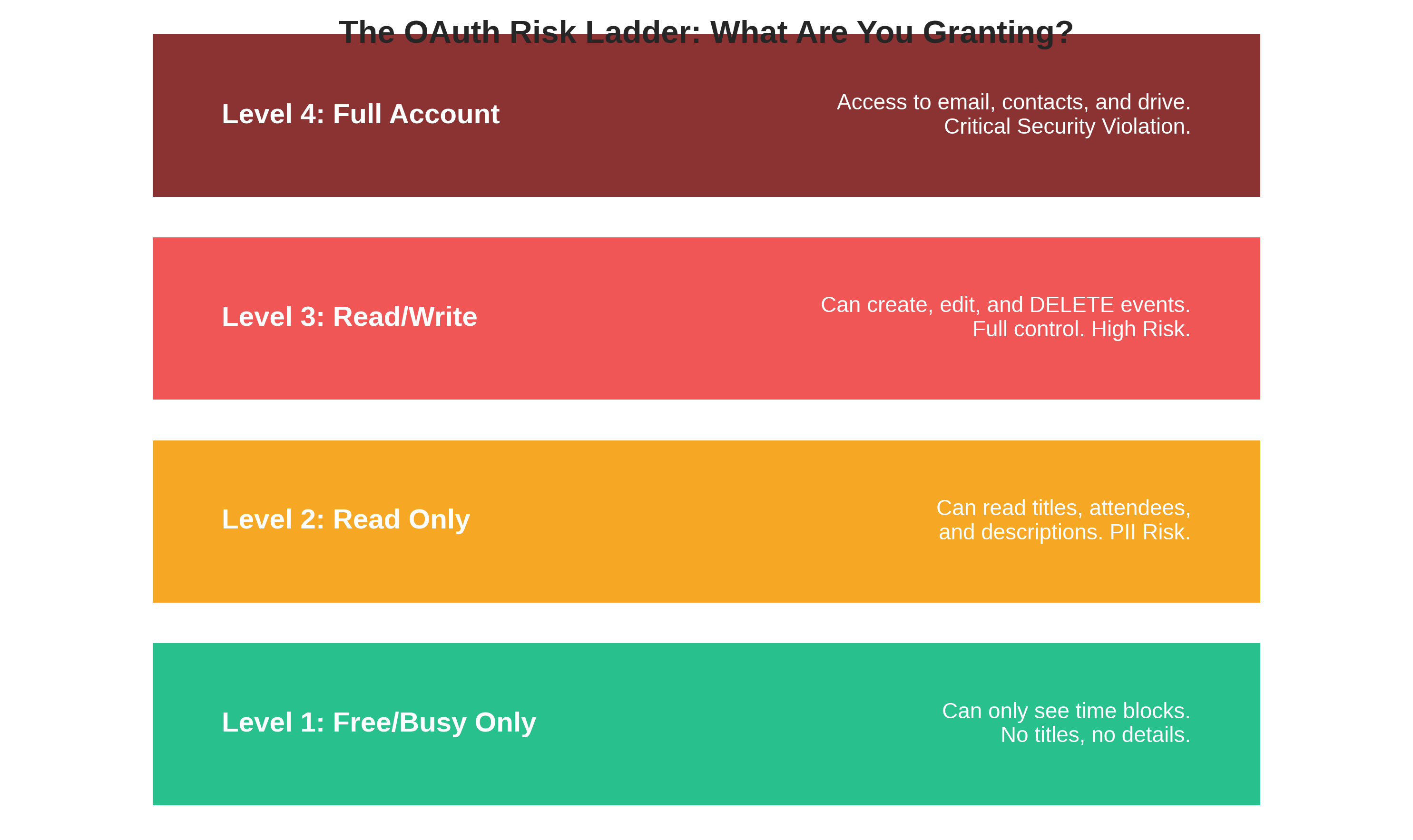
When a SaaS tool requests https://www.googleapis.com/auth/calendar (Google) or Calendars.ReadWrite (Microsoft), they are not just seeing "Busy" slots. They technically have access to:
- Meeting Details & AttachmentsTitles like "Acquisition Strategy w/ Competitor X" or "Layoff Planning" are visible. Some scopes even allow reading attachments linked in invites.
- Attendee Lists (PII Exposure)The tool can scrape the email addresses of every external client, partner, or investor you meet with. This is a massive GDPR/CCPA liability.
- Modification Rights"Write" access means the tool can delete existing meetings or send invites on your behalf without further prompting.
The "Least Privilege" Alternative
You don't have to accept the default. Mature enterprise scheduling platforms offer granular scopes. When evaluating a vendor, ask if they support:
1. Free/Busy Only
The tool only sees that you are busy, not why. It cannot read titles, descriptions, or attendees. This is the gold standard for privacy but limits functionality (e.g., the tool can't prevent conflicts based on meeting types).
2. Service Account Integration
Instead of every user granting OAuth tokens, IT connects a single Service Account with restricted scopes. This centralizes control and allows instant revocation of access for the entire org.
The "Shadow IT" Vector
The biggest risk isn't the tool you buy officially; it's the free tools your employees sign up for. When a sales rep connects their work calendar to a random "AI Scheduling Assistant" they found on Product Hunt, they bypass your procurement checks.
Actionable Policy for IT Admins:
- Audit OAuth Tokens: Regularly check Google Workspace / Microsoft 365 admin consoles for unauthorized third-party apps.
- Block by Default: Configure your tenant to block all third-party calendar access unless the App ID is explicitly allow-listed.
- Educate on "Consent Phishing": Train staff that granting calendar access is equivalent to sharing their password.
Final Thought for the CIO
Convenience is the enemy of security. A scheduling tool that "just works" without asking for permissions is likely over-privileged. The friction of configuring granular scopes is the price of data sovereignty.